Advanced Persistent Threat: How Cybercriminals Move
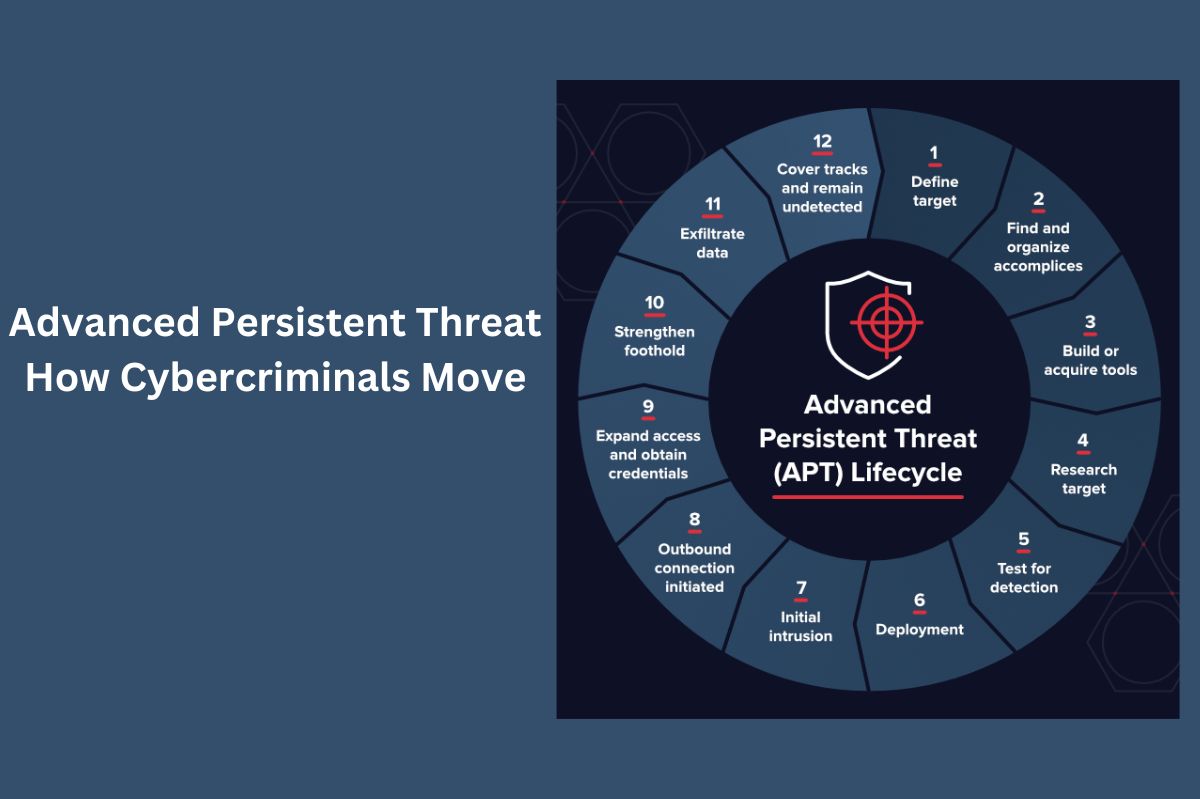
The definition of Advanced Persistent Threat (APT) is hotly debated in the field of cybersecurity. In the beginning, APTs meant types of attacks generated by nation-states, but the term has started to include the illicit activities perpetrated by gangs of organized cybercriminals who intend to evade the security controls of companies with high-security standards, such as example, financial institutions.
Over time, advanced techniques will be adopted by less advanced attackers, meaning enterprises will need to step up security controls and investments to prevent these attacks. Advanced threat actors will then be able to develop new attack techniques to bypass these new controls, resulting in the never-ending game of cat and mouse.
APT attack types
The latest research shows that cybercriminal gangs, such as Metel, GCMAN, and Carbanak, adopt APT attack techniques to commit financial crimes. The steps these groups are taking include the following:
- Reconnaissance.
- The development of social engineering techniques.
- The creation of specialized malware and tools to carry out persistent and long-term attacks through lateral movements.
The reconnaissance phase takes place before planning the attack and understanding how to customize the social engineering phase to make it more effective. The malware is first tested against antimalware tools to see if it can evade detection systems. Lateral network movements are used to identify systems that control critical operations or that store sensitive data that could then be monetized. Long-term persistence is a useful technique for monetizing APT attacks over time, minimizing the chance of attackers being discovered and caught.
The Carbanak gang uses social engineering techniques through a phishing email that includes an attachment to initially set foot on the network of a large company and then, through monitoring, allow identifying the location of sensitive data to modify its own criteria. Metal uses malware to intercept ATM (Automated Teller Machine) transactions and hack operations via ATMs. GCMAN exploits lateral movement, starting with web servers and compromising other internal hosts long-term before monetizing.
Enterprises can protect themselves from Advanced Persistent Threats
The primary techniques used for these APT attacks have stayed the same over time, and enterprise security systems likely already have controls in place to protect data against some APT attacks using reconnaissance, social engineering, specialized malware, and lateral movement. Enterprises should examine each step during an attack to see if their security controls can prevent it.
If controls are found to be ineffective, organizations should conduct a risk assessment to determine the reasons for their inadequacy, understand how to improve controls, and quantify the costs of improving controls. Precisely speaking of these issues, Richard Turner, EMEA President of FireEye, during the presentation of the annual report on the latest generation of cyber threats, said:
“The threat landscape changes every day, and organizations must use every opportunity to try to stay one step ahead of attackers. The evidence highlighted in this report demonstrates that the geopolitical, economic, and financial changes taking place in the region are increasingly being mirrored in the cybersecurity world. Organizations are all the stronger the more their adaptability is developed. For this reason, it is essential to have the right tools to return to normality as quickly as possible in the event of a violation “.
Also Read : Ethical Hacking: Security Services To Test The Infrastructure
